What We Do
“Cyber Defense Assistance” (CDA) refers to targeted cyber support activities provided to friendly or allied nation-states under attack or threat from a hostile nation-state and requires collaboration with the private sector for its delivery and success.
cyber defense Assistance
To date, cyber defense assistance has been aimed at meeting more immediate needs—primarily providing operational cyber support to Ukraine in the run-up to and early stages of Russia’s February 2022 invasion. However, the CDA model is built in such a way that it can be applied to other conflicts, and activity will not always be exigent, and can take the form of pre- or post-conflict capability enhancements. Nonetheless conflict-driven national security objectives should always guide CDA decision-making.
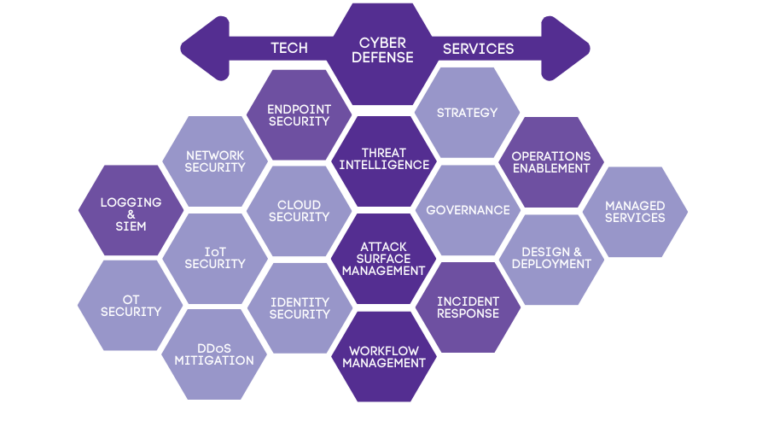
Activities include: Vulnerability Management (VM), Security Information and Event Management (SIEM), Distributed Denial of Service (DDoS) Management, Cyber Threat Intelligence, Attack Surface Monitoring (ASM), Executive Engagement, Malware Forensics, Compromise Assessment and Incident Response (CAIR), Endpoint Detection and Response (EDR), Security Operations Centers (SOCs), Industrial Control System (ICS) Cybersecurity

cyber defense Assistance
To date, cyber defense assistance has been aimed at meeting more immediate needs—primarily providing operational cyber support to Ukraine in the run-up to and early stages of Russia’s February 2022 invasion. However, the CDA model is built in such a way that it can be applied to other conflicts, and activity will not always be exigent, and can take the form of pre- or post-conflict capability enhancements. Nonetheless conflict-driven national security objectives should always guide CDA decision-making.
Activities include: Vulnerability Management (VM), Security Information and Event Management (SIEM), Distributed Denial of Service (DDoS) Management, Cyber Threat Intelligence, Attack Surface Monitoring (ASM), Executive Engagement, Malware Forensics, Compromise Assessment and Incident Response (CAIR), Endpoint Detection and Response (EDR), Security Operations Centers (SOCs), Industrial Control System (ICS) Cybersecurity

Core Capabilities